आपका डेटा है संरक्षित
मेवेज़ में, हम सुरक्षा और डेटा सुरक्षा को गंभीरता से लेते हैं। हम आपके डेटा की सुरक्षा और आपकी गोपनीयता सुनिश्चित करने के लिए उद्योग-मानक सुरक्षा उपाय लागू करते हैं।
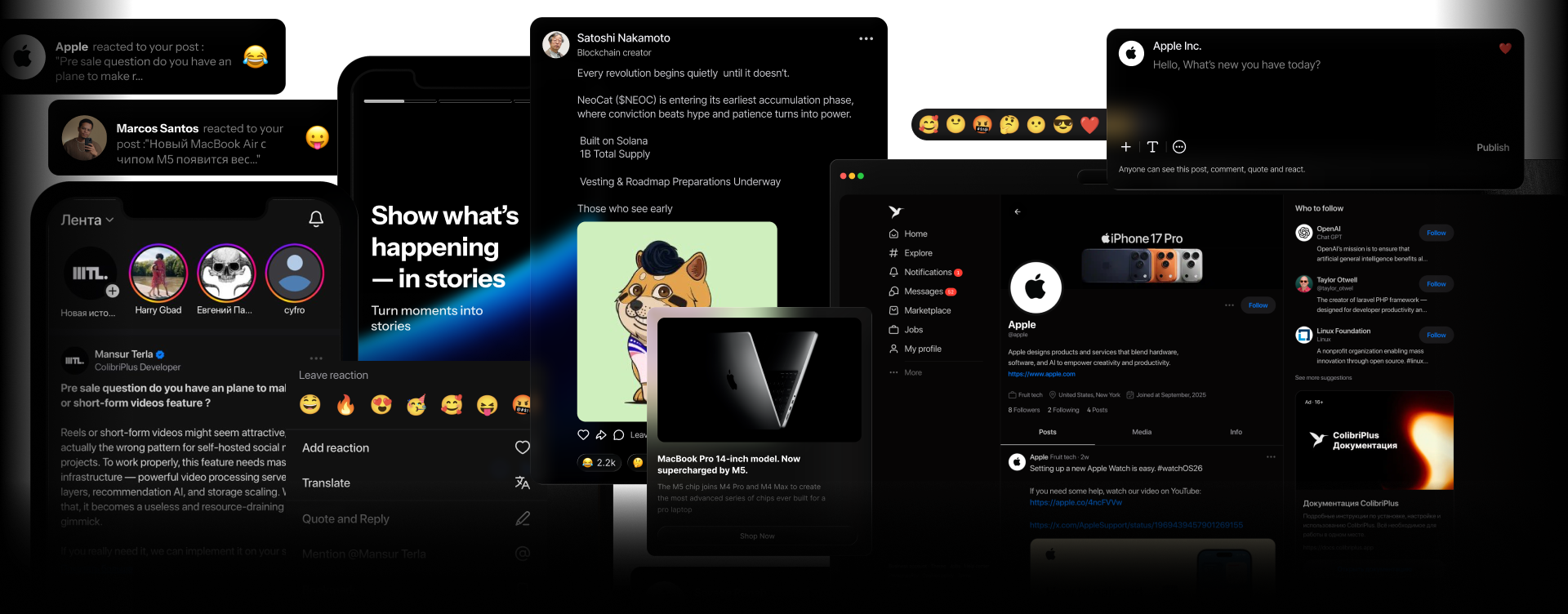
मंच को क्रियान्वित होते हुए देखें
मेवेज़ सोशल पर एक साथ काम करने के लिए पोस्ट, कहानियां, मैसेजिंग, मार्केटप्लेस और बहुत कुछ बनाया गया है।
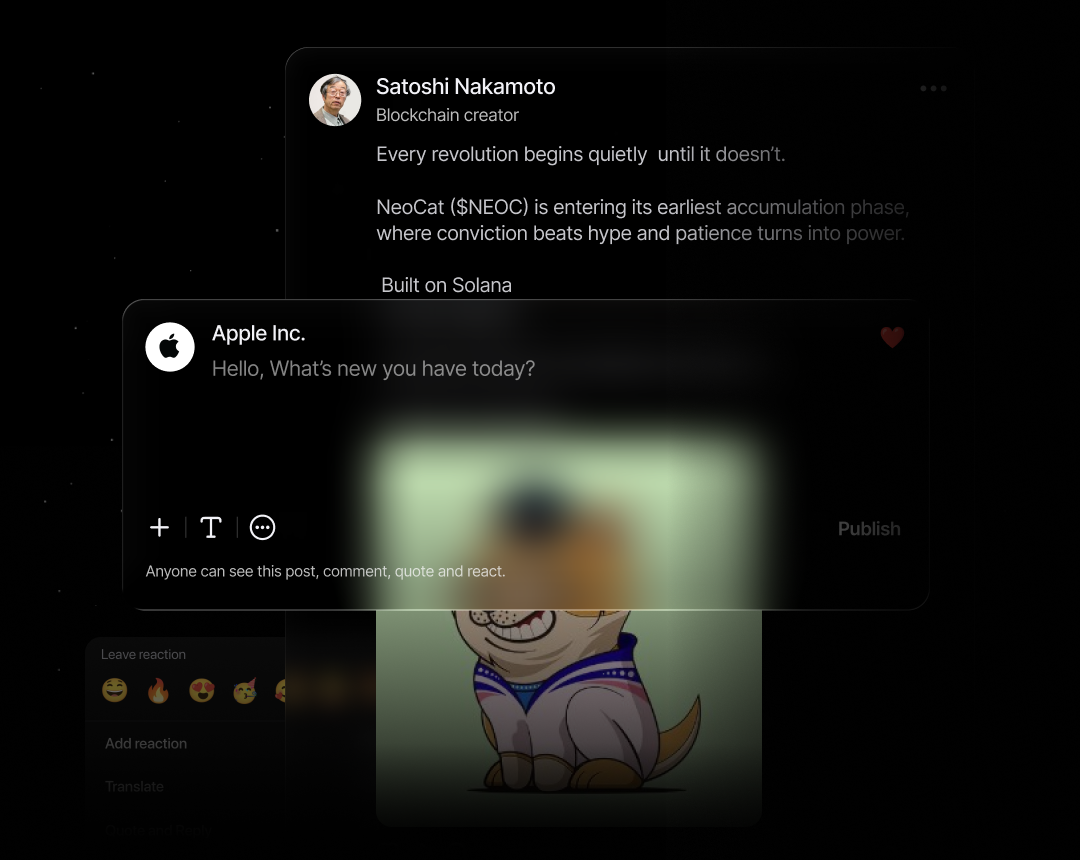
पोस्ट और टाइमलाइन
टेक्स्ट, फ़ोटो, वीडियो, पोल और लिंक साझा करें। प्रतिक्रियाएँ, टिप्पणियाँ और पुनः साझाकरण प्राप्त करें।

कहानियां
लघु रूप वाली कहानियाँ प्रकाशित करें। जहां कॉन्फ़िगर किया गया हो वहां ट्रैकिंग और अल्पकालिक सामग्री देखें।
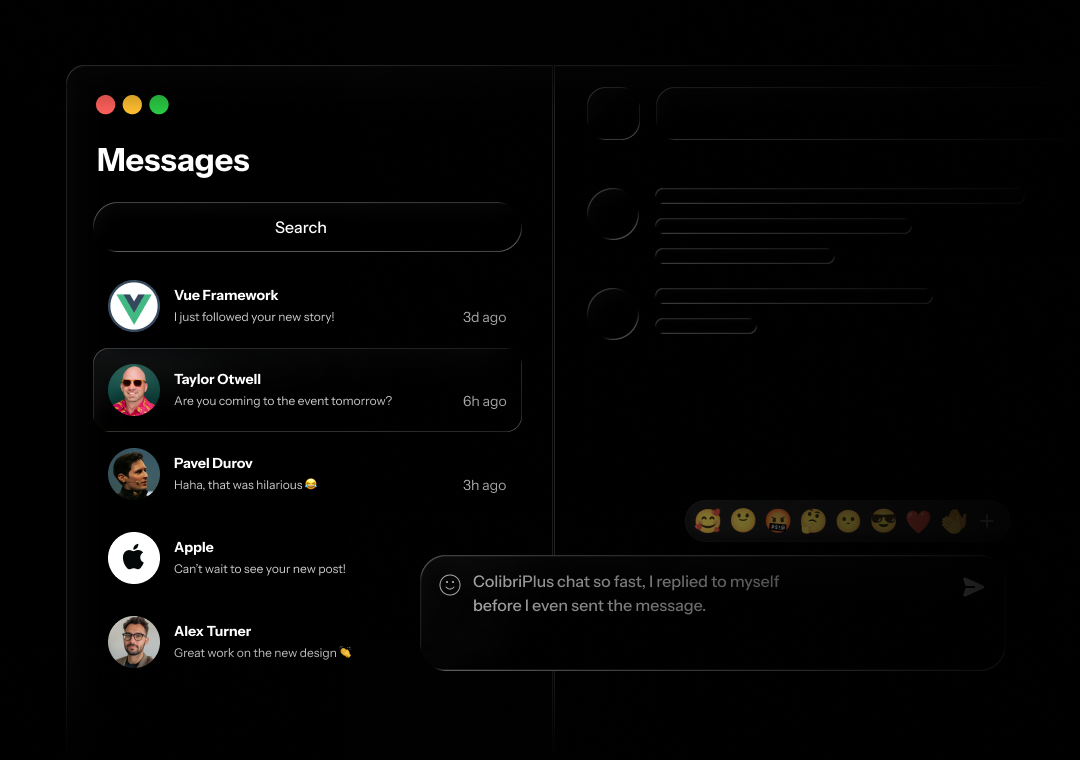
मैसेंजर
मीडिया, टाइपिंग संकेतक और वास्तविक समय सिंक के साथ सीधे संदेश और समूह चैट।
सूचनाएं
संदेशों, टिप्पणियों, उल्लेखों और गतिविधि पर अपडेट रहें।
विज्ञापन
जहां उपलब्ध हो वहां व्यवसाय डैशबोर्ड से प्रचार चलाएं और विज्ञापन प्रबंधित करें।
बाज़ार और नौकरियाँ
उत्पादों की सूची बनाएं, बाज़ार ब्राउज़ करें, और नौकरी लिस्टिंग प्रकाशित करें या खोजें।
विस्तृत सुरक्षा उपाय
हम आपके डेटा की सुरक्षा और आपकी गोपनीयता सुनिश्चित करने के लिए सुरक्षा की कई परतें लागू करते हैं।
डेटा एन्क्रिप्शन
सुरक्षित भंडारण
गोपनीयता अनुपालन
अभिगम नियंत्रण
सुरक्षा ऑडिट
घटना प्रतिक्रिया
डेटा कूटलेखन
आपके डिवाइस और हमारे सर्वर के बीच प्रसारित सभी डेटा एसएसएल/टीएलएस प्रोटोकॉल का उपयोग करके एन्क्रिप्ट किया गया है। हम आपकी संवेदनशील जानकारी की सुरक्षा के लिए मजबूत एन्क्रिप्शन एल्गोरिदम का उपयोग करते हैं।
हमारे एन्क्रिप्शन मानक उद्योग की सर्वोत्तम प्रथाओं को पूरा करते हैं, यह सुनिश्चित करते हुए कि ट्रांसमिशन के दौरान आपका डेटा सुरक्षित रहे। हम बाकी डेटा के लिए AES-256 एन्क्रिप्शन और ट्रांज़िट में डेटा के लिए TLS 1.3 का उपयोग करते हैं।
सुरक्षित भंडारण
आपका डेटा सुरक्षा की कई परतों के साथ हमारे सर्वर पर सुरक्षित रूप से संग्रहीत है। संभावित खतरों से बचने के लिए हम नियमित रूप से अपने सुरक्षा उपायों को अपडेट करते हैं।
हमारा बुनियादी ढांचा अनावश्यक बैकअप के साथ सुरक्षित, एंटरप्राइज़-ग्रेड सर्वर पर होस्ट किया गया है। हम आपके डेटा को अनधिकृत पहुंच से बचाने के लिए एक्सेस नियंत्रण, फ़ायरवॉल और घुसपैठ का पता लगाने वाले सिस्टम लागू करते हैं।
नियमित बैकअप यह सुनिश्चित करता है कि आपका डेटा सुरक्षित है और किसी भी अप्रत्याशित घटना के मामले में उसे पुनर्प्राप्त किया जा सकता है। हम भौगोलिक रूप से वितरित स्थानों में कई बैकअप प्रतियां बनाए रखते हैं।
गोपनीयता अनुपालन
हम जीडीपीआर और अन्य गोपनीयता नियमों का अनुपालन करते हैं। आपकी व्यक्तिगत जानकारी हमारी गोपनीयता नीति के अनुसार संभाली जाती है, और आपके डेटा पर आपका नियंत्रण होता है।
हम आपकी व्यक्तिगत जानकारी कैसे एकत्र करते हैं, उसका उपयोग करते हैं और उसकी सुरक्षा कैसे करते हैं, इस बारे में पारदर्शिता के लिए प्रतिबद्ध हैं। आप अपनी खाता सेटिंग के माध्यम से किसी भी समय अपने डेटा तक पहुंच सकते हैं, अपडेट कर सकते हैं या हटा सकते हैं।
हमारी गोपनीयता नीति आपके व्यक्तिगत डेटा के संबंध में आपके अधिकारों और हमारी जिम्मेदारियों को स्पष्ट रूप से रेखांकित करती है। हम आपकी व्यक्तिगत जानकारी तीसरे पक्ष को नहीं बेचते हैं।
नियमित सुरक्षा ऑडिट
हम संभावित कमजोरियों की पहचान करने और उन्हें ठीक करने के लिए नियमित सुरक्षा ऑडिट और प्रवेश परीक्षण करते हैं। हमारी सुरक्षा टीम 24/7 हमारे सिस्टम की निगरानी करती है।
हम व्यापक सुरक्षा मूल्यांकन करने के लिए स्वतंत्र सुरक्षा फर्मों के साथ काम करते हैं। पाई गई किसी भी कमज़ोरी का तुरंत समाधान किया जाता है और उसे ठीक किया जाता है।
हमारी सुरक्षा निगरानी में वास्तविक समय में खतरे का पता लगाना, स्वचालित अलर्ट और घटना प्रतिक्रिया प्रक्रियाएं शामिल हैं। हम विस्तृत सुरक्षा लॉग और ऑडिट ट्रेल्स बनाए रखते हैं।
पहुँच नियंत्रण
हम यह सुनिश्चित करने के लिए सख्त पहुंच नियंत्रण लागू करते हैं कि केवल अधिकृत कर्मचारी ही आपके डेटा तक पहुंच सकें। सभी पहुंच लॉग और मॉनिटर की जाती है।
हमारी टीम के सदस्य पृष्ठभूमि की जांच और सुरक्षा प्रशिक्षण से गुजरते हैं। संवेदनशील डेटा तक पहुंच जानने की आवश्यकता के आधार पर दी जाती है और नियमित रूप से समीक्षा की जाती है।
घटना प्रतिक्रिया
किसी सुरक्षा घटना की अप्रत्याशित स्थिति में, हमारे पास एक व्यापक घटना प्रतिक्रिया योजना है। हम प्रभावित उपयोगकर्ताओं को तुरंत सूचित करेंगे और किसी भी जोखिम को कम करने के लिए तत्काल कार्रवाई करेंगे।
हमारी घटना प्रतिक्रिया टीम को सुरक्षा घटनाओं को जल्दी और प्रभावी ढंग से संभालने के लिए प्रशिक्षित किया गया है। हम आपको सुरक्षा संबंधी किसी भी मामले के बारे में सूचित रखने के लिए संचार चैनल बनाए रखते हैं।
मदद की ज़रूरत है?
सुरक्षा के बारे में प्रश्न?
हमारी सुरक्षा टीम मदद के लिए यहां है। यदि हमारे सुरक्षा उपायों के बारे में आपके कोई प्रश्न हों तो हमसे संपर्क करें।